Process Hacker 是一款功能强大的开源进程和系统监控工具,专为 Windows 设计。它提供高级功能,用于检查进程、监控系统资源、管理服务和调试系统问题。
与基础任务管理器不同,Process Hacker 提供对系统操作的深入洞察,是任何需要了解 Windows 系统底层运行情况的用户的必备工具。
重要提示: Process Hacker 是一款合法的开源系统监控工具。它不是恶意软件、间谍软件或任何形式的恶意程序。它专为合法的系统管理、调试和监控目的而设计。
超越标准任务管理器的强大功能
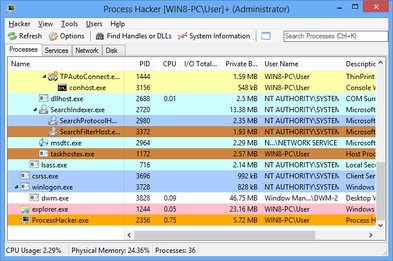
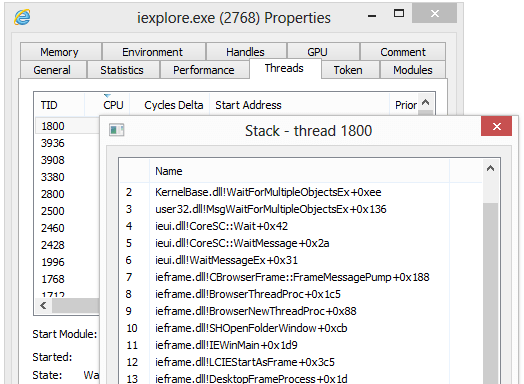
深入了解进程详情,包括线程、句柄、内存映射和已加载模块。查看实时进程信息,具备全面的调试功能。
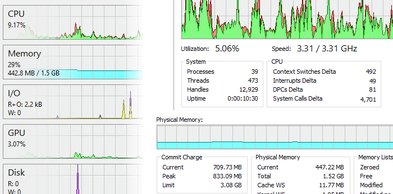
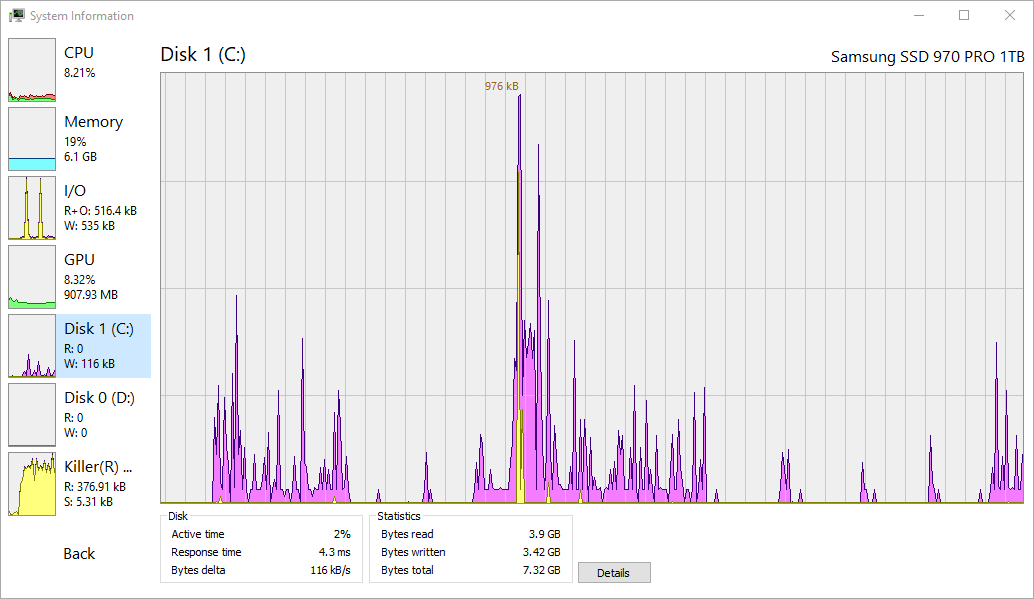
实时监控 CPU、内存、磁盘 I/O 和网络活动。通过详细的图表和统计数据跟踪系统资源,进行全面的性能分析。
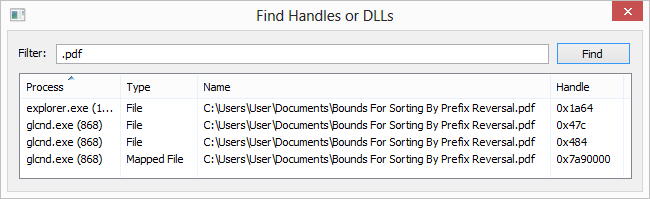
管理进程权限、令牌信息和安全上下文。查看和修改访问权限,提供详细的安全描述符信息。
详细的性能指标,包括每个核心的 CPU 使用率、内存消耗模式、磁盘 I/O 统计和网络吞吐量分析。
支持插件的可扩展架构。通过自定义插件扩展功能,用于专门的监控、分析和系统管理任务。
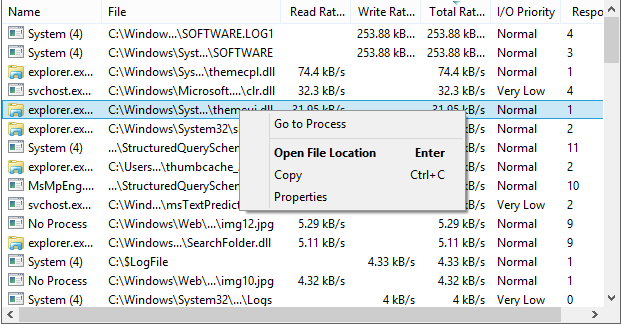
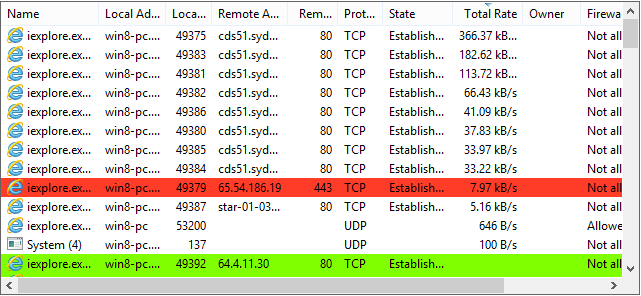
监控网络连接,查看活动的 TCP/UDP 连接,并按进程分析网络活动。识别网络相关问题和可疑连接。
了解 Process Hacker 如何帮助专业人士解决实际问题
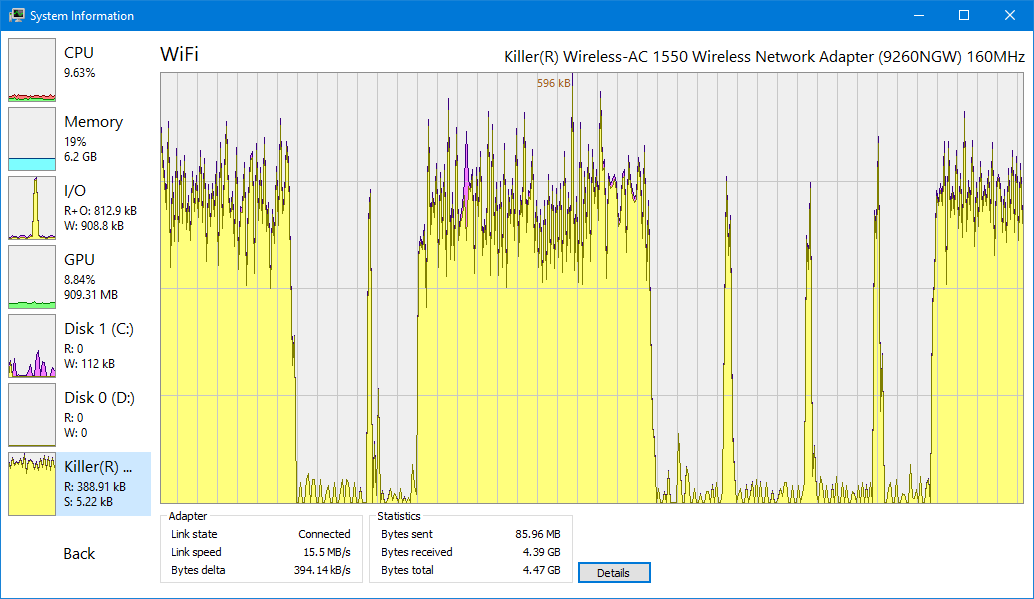
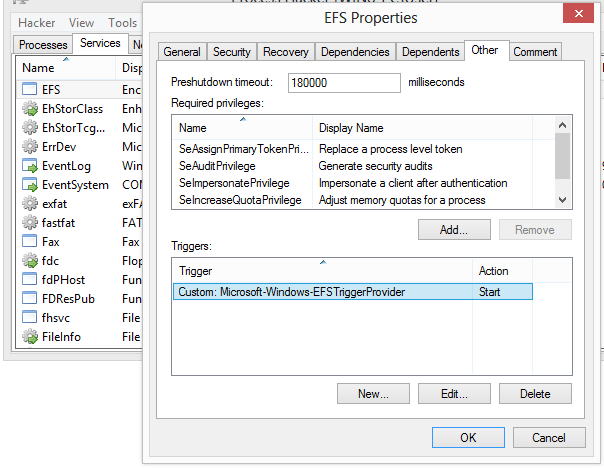
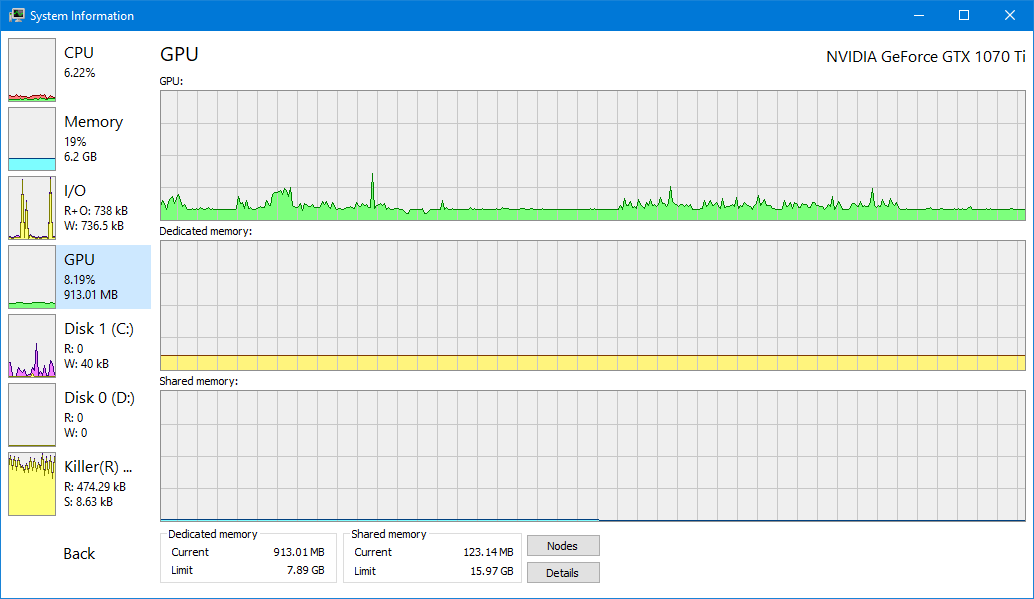
See how Process Hacker compares to Windows Task Manager
| Feature | Process Hacker | Windows Task Manager |
|---|---|---|
| Process Details | Comprehensive | Basic |
| Thread Information | ✓ Full Details | Limited |
| Handle Inspection | ✓ Available | ✗ Not Available |
| Memory Maps | ✓ Available | ✗ Not Available |
| Network Connections | ✓ Per Process | System-wide Only |
| Service Management | ✓ Advanced | Basic |
| Token & Security Info | ✓ Available | ✗ Not Available |
| Plugin Support | ✓ Extensible | ✗ Not Available |
| Performance Graphs | ✓ Detailed | Basic |
| Open Source | ✓ Yes | No |
Common problems and step-by-step solutions
Problem:
Your system is running slow, and you suspect a process is consuming too much CPU.
Solution:
Problem:
System memory is gradually being consumed, and you suspect a memory leak.
Solution:
Problem:
You want to identify which processes are making network connections.
Solution:
Problem:
A Windows service is not starting or behaving unexpectedly.
Solution:
Problem:
A file cannot be deleted or modified because it's locked by a process.
Solution:
Get the latest version of Process Hacker - completely free and open-source
Process Hacker is actively maintained and regularly updated with new features and security improvements.
立即下载Process Hacker is open-source software. All source code is available on GitHub for review, audit, and contribution. You can verify exactly what the software does.
Process Hacker is a legitimate system monitoring tool. It does not contain malware, spyware, or any malicious components. Always download from the official GitHub repository.
Important: Only download Process Hacker from the official GitHub repository. Be cautious of third-party download sites that may distribute modified or malicious versions.
Common questions about Process Hacker
Yes, Process Hacker is completely safe to use. It is a legitimate, open-source system monitoring tool. The source code is publicly available on GitHub, allowing anyone to review and verify its functionality. Process Hacker does not contain malware, spyware, or any malicious components. However, always download from the official GitHub repository to ensure you're getting the authentic version.
Process Hacker can run without administrator privileges for basic monitoring tasks. However, many advanced features require administrator rights, including:
For the best experience and full functionality, it's recommended to run Process Hacker with administrator privileges.
Process Hacker offers significantly more advanced features than Windows Task Manager:
While Task Manager is great for basic tasks, Process Hacker is designed for power users, developers, and system administrators who need deeper insights.
Yes, Process Hacker is completely free and open-source. It is released under the GNU General Public License (GPL), which means you can use, modify, and distribute it freely. There are no hidden costs, subscriptions, or premium versions.
Process Hacker is a legitimate system administration and debugging tool. Like any powerful tool, it could potentially be misused, but it is designed and intended for legitimate purposes such as:
Process Hacker should only be used on systems you own or have explicit permission to monitor. Unauthorized use on systems you don't own or have permission to access is illegal and unethical.
Process Hacker is designed for modern Windows operating systems. It supports:
Some features may require specific Windows versions or service packs. Check the GitHub repository for the most up-to-date compatibility information.
Process Hacker is an open-source project, and contributions are welcome! You can contribute in several ways:
Visit the official GitHub repository to learn more about contributing guidelines and the development process.
Transparency, security, and responsible use
Process Hacker is a legitimate system administration and debugging tool. It is designed for authorized system monitoring, troubleshooting, and development purposes.
Important: Only use Process Hacker on systems you own or have explicit written permission to monitor. Unauthorized access to or monitoring of computer systems without permission is illegal in most jurisdictions and may violate computer fraud and abuse laws.
Process Hacker is fully open-source software. The complete source code is available on GitHub, allowing anyone to:
This transparency ensures that Process Hacker can be trusted and verified by the community.
Process Hacker is NOT malware, spyware, adware, or any form of malicious software. It does not:
Some antivirus software may flag Process Hacker due to its powerful system access capabilities. This is a false positive - Process Hacker's capabilities are similar to those of legitimate system administration tools. If you encounter such warnings, you can safely add Process Hacker to your antivirus exclusion list.
Process Hacker prioritizes security and privacy: