Advanced Process & System Monitoring
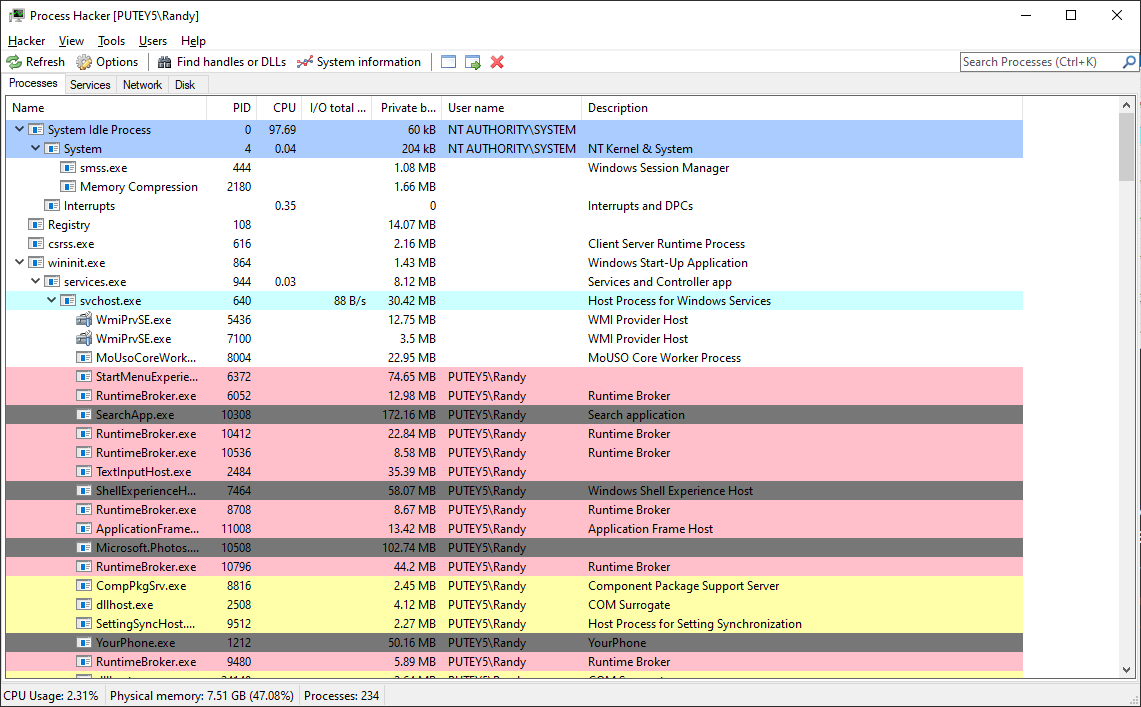
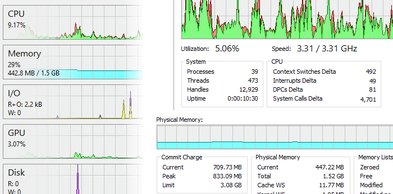
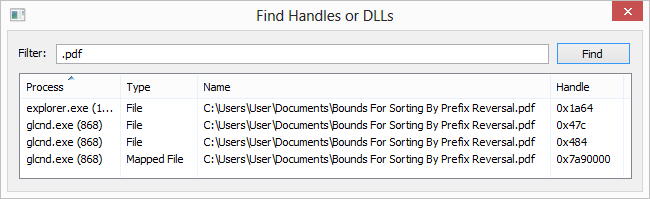
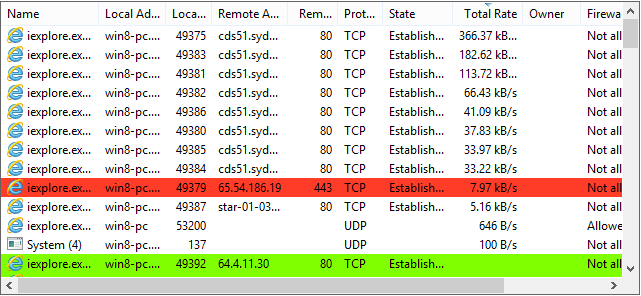
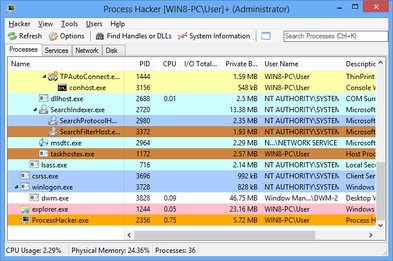
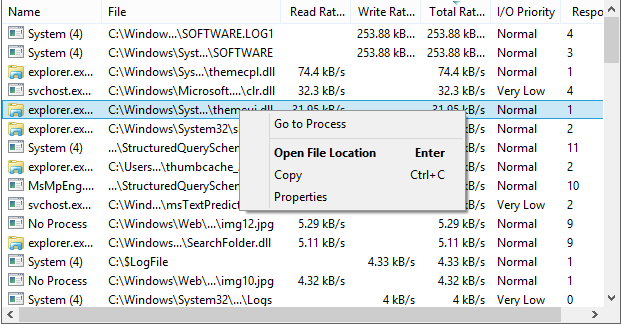
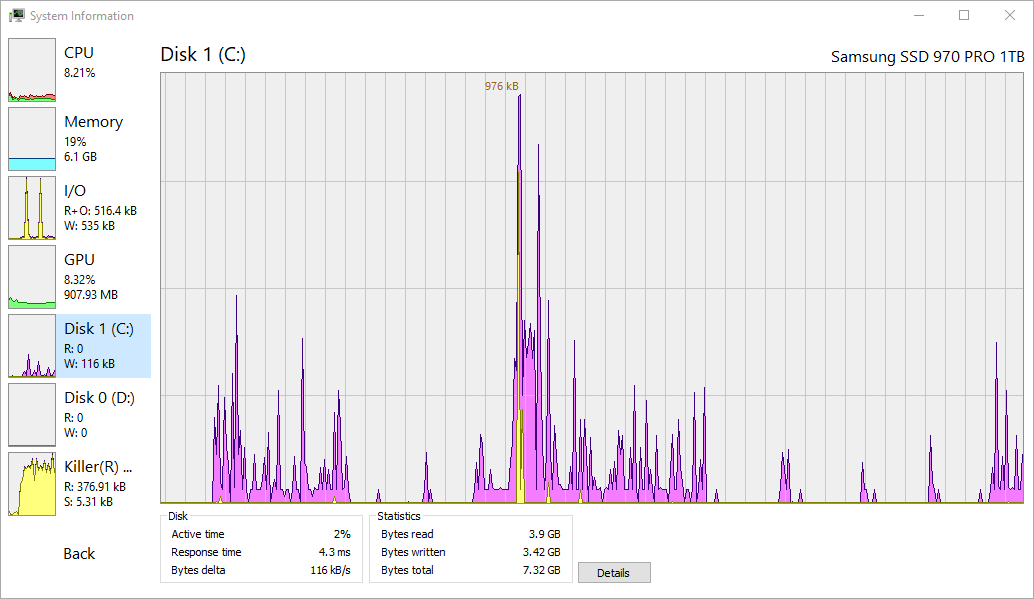
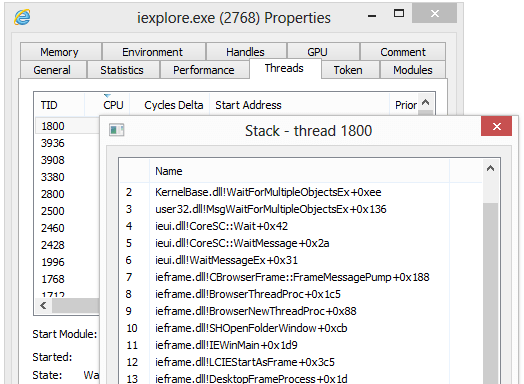
Professional-grade tool for monitoring processes, services, network connections, and system performance on Windows.
Trusted by developers, system administrators, and power users worldwide. Open-source, transparent, and secure.